

Brad Smith, Microsoft’s President and Chief Legal Officer, blasted the U.S. National Security Agency (NSA) in a recent blog post, which is said to have lost control of its hacking tools, for the WannaCrypt exploits used in the massive cyberattack that crippled hospitals, businesses, governments, and personal computers around the world. He called on governments to report vulnerabilities to vendors, rather than stockpile, sell, or exploit them.
In his blog post, Smith wrote that governments “should treat this attack as a wake-up call.” “They need to take a different approach and adhere in cyberspace to the same rules applied to weapons in the physical world.”
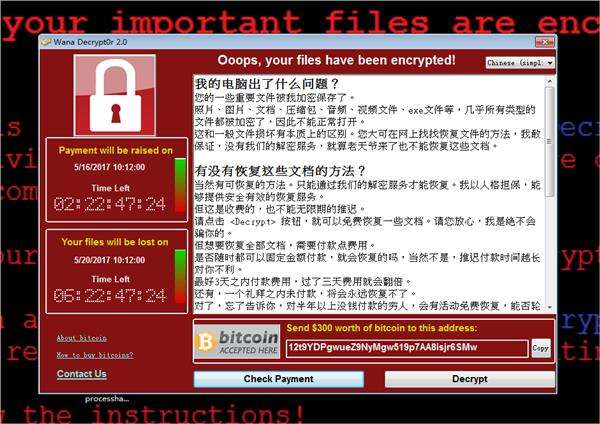
The NSA-powered WannaCry exploit is a type of computer malware known as “ransomware,” which is software that demands a “ransom” after gaining control of the affected computer. The malware exploits a previously unknown vulnerability in the Windows operating system.
The unprecedented attack, which began infecting computers on Friday, May 12, has hit more than 200,000 computers in at least 150 countries, and the threat is escalating. Check Point Software said on Monday that a new variant is now infecting computers at rate of about one per second, or about 3,600 per hour, according to a report by Reuters.
There are a lot of theories about who is behind the attack, but no definitive evidence. Researchers at Kaspersky and Symantec both said on Monday that they found similarities between WannaCry and previous code used by a North Korean hacking group known as Lazarus. But shared code doesn’t necessarily mean that the same group is responsible. Hackers often use “false flags” to confuse security experts. In March, for example, Wikileaks revealed documents that it says show the U.S. Central Intelligence Agency (CIA) runs secret false-flag hacking operations to falsely attribute attacks to other actors, such as Russia and China.
Security experts have yet to identify who was behind the attack, but China was hit particularly hard. There has been some speculation on Chinese social media that the attack was meant to target the Belt and Road Forum for International Cooperation, which was held in Beijing on May 14 and 15, though there has not been any solid evidence to back up this claim and no Chinese officials have made such comments. But if true, that might suggest that the NSA-powered cyberattack was carried out to derail China’s efforts at creating a new type of international relations with its Belt and Road Initiative.
Regardless of who was behind the attack, the latest global incident has created urgency for enhancing cybersecurity and global cooperation. On the day of the attack, U.S. Representative Ted Lieu said it was “deeply distributing” that the NSA “likely wrote the original malware” in a written statement, adding that the attack “shows what can happen when the NSA or CIA write malware instead of disclosing the vulnerability to the software manufacturer.”
Xiakedao, a WeChat news account run by the People’s Daily, urged the NSA to draw lessons from the attack, and called the “black box” decision-making process within the U.S. government about whether to disclose a software vulnerability “worthy of criticism” and “problematic,” because the whole world is put at risk by an internal decision within the U.S. government.
China has long called for enhanced cybersecurity and the establishment of a rules-based order in cyberspace. Like the real world, China wants governments to work together to formulate universally accepted international rules and norms of state behavior.

 Award-winning photos show poverty reduction achievements in NE China's Jilin province
Award-winning photos show poverty reduction achievements in NE China's Jilin province People dance to greet advent of New Year in Ameiqituo Town, Guizhou
People dance to greet advent of New Year in Ameiqituo Town, Guizhou Fire brigade in Shanghai holds group wedding
Fire brigade in Shanghai holds group wedding Tourists enjoy ice sculptures in Datan Town, north China
Tourists enjoy ice sculptures in Datan Town, north China Sunset scenery of Dayan Pagoda in Xi'an
Sunset scenery of Dayan Pagoda in Xi'an Tourists have fun at scenic spot in Nanlong Town, NW China
Tourists have fun at scenic spot in Nanlong Town, NW China Harbin attracts tourists by making best use of ice in winter
Harbin attracts tourists by making best use of ice in winter In pics: FIS Alpine Ski Women's World Cup Slalom
In pics: FIS Alpine Ski Women's World Cup Slalom Black-necked cranes rest at reservoir in Lhunzhub County, Lhasa
Black-necked cranes rest at reservoir in Lhunzhub County, Lhasa China's FAST telescope will be available to foreign scientists in April
China's FAST telescope will be available to foreign scientists in April